Introduction
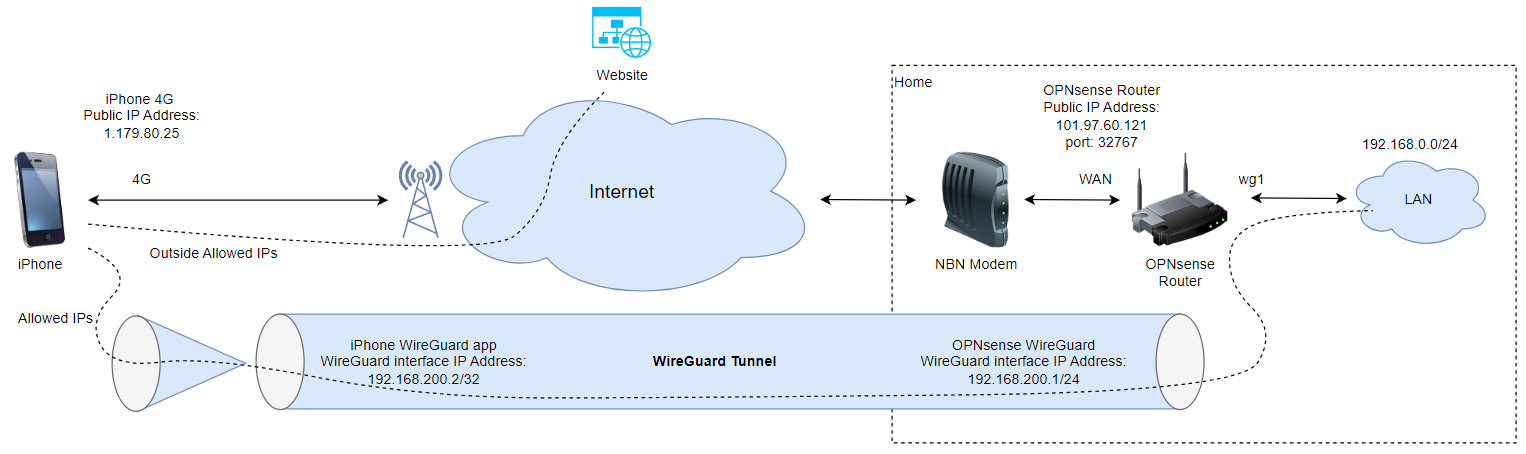
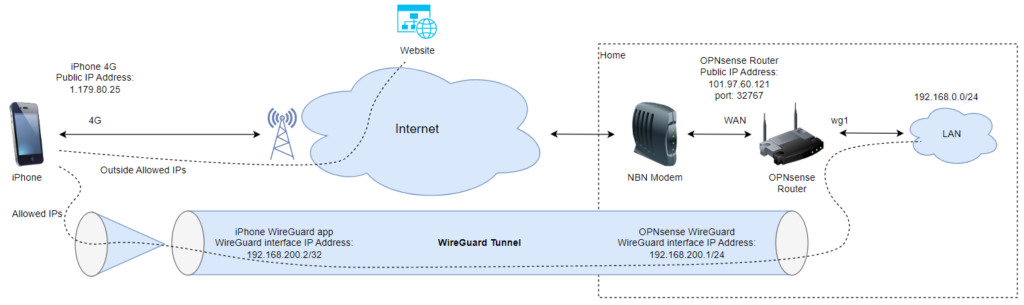
This guide explains how to connect your iPhone to your home network securely using WireGuard on OPNsense.
Diagram
Settings
OPNsense WireGuard Instance Settings
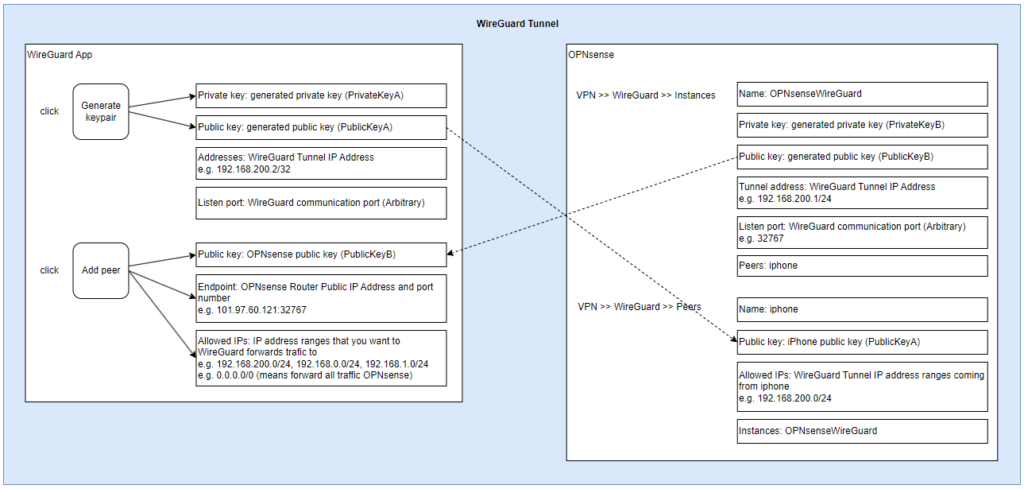
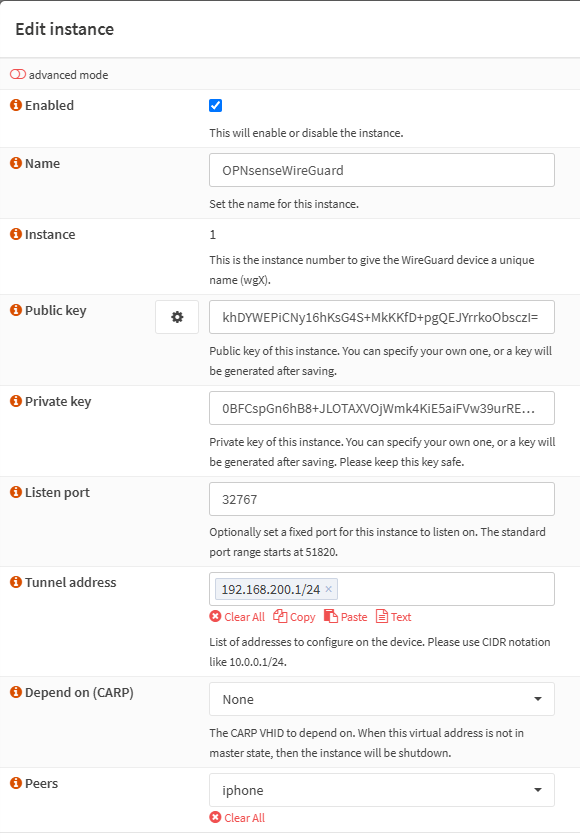
In OPNsense, go to VPN -> WireGuard -> Instances -> + Add
- Public key and Private key can be generated by clicking the “cog” icon button (next to Public key).
- Listen port: port WireGuard listens to at public IP address.
- 32767 in this example.
- Tunnel address: WireGuard interface address
- 192.168.200.1/24 in this example.
- Peers: peer name linked with this WireGuard instance.
Mobile WireGuard App Settings
In Mobile WireGuard App, click + to add.
- You could choose “Create from QR code” and scan the QR code on OPNsense Peer generator page (VPN -> WireGuard -> Peer generator). I had error saying invalid QR code. So I had to choose “Create from scratch”.
- The ‘Create from Scratch’ option.
- Click “Generate kaypair” to generate Public and Private keys.
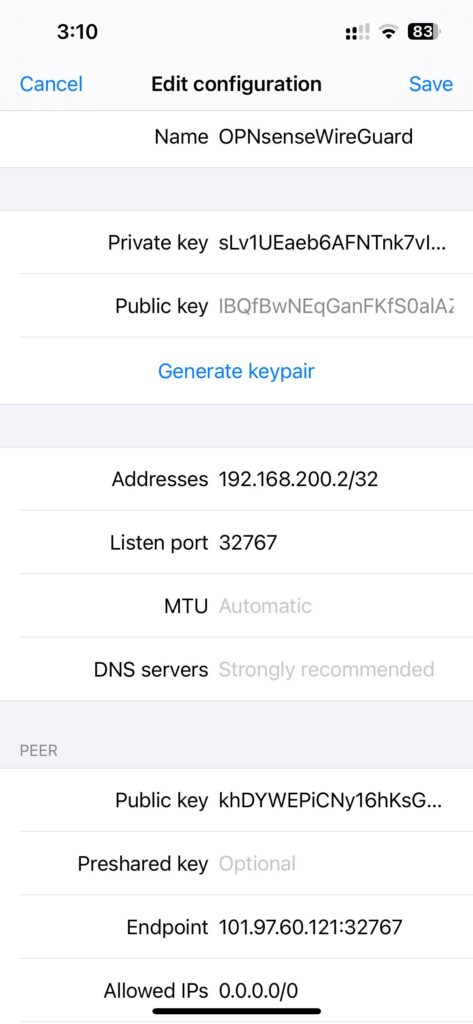
- Addresses: iPhone WireGuard interface address for this tunnel.
- 192.168.200.2/32 in this example.
- Listen port: 32767 in this example.
- DNS Server: DNS server in your LAN
- 192.168.200.1 in this example.
- Click “Add peer” to setup OPNsense WireGuard peer
- Public Key: OPNsense WireGuard Instance Public key
- Endpoint: public IP address of OPNsense WAN interface and WireGuard listen port number.
- 101.97.60.121:32767 in this example.
- Allowed IPs: IP range you want WireGuard app to forward to OPNsense.
- 192.168.200.0/24, 192.168.0.0/24, 192.168.1.0/24 means forward LAN traffic all traffic to OPNsense WireGuard. (Assuming LAN network addresses are 192.168.0.0/24, 192.168.1.0/24)
- If you want to redirect all your data traffic from your iPhone to OPNsense WireGuard, put 0.0.0.0/0 here. But it requires OPNsense NAT setup to work.
OPNsense WireGuard Peer Settings
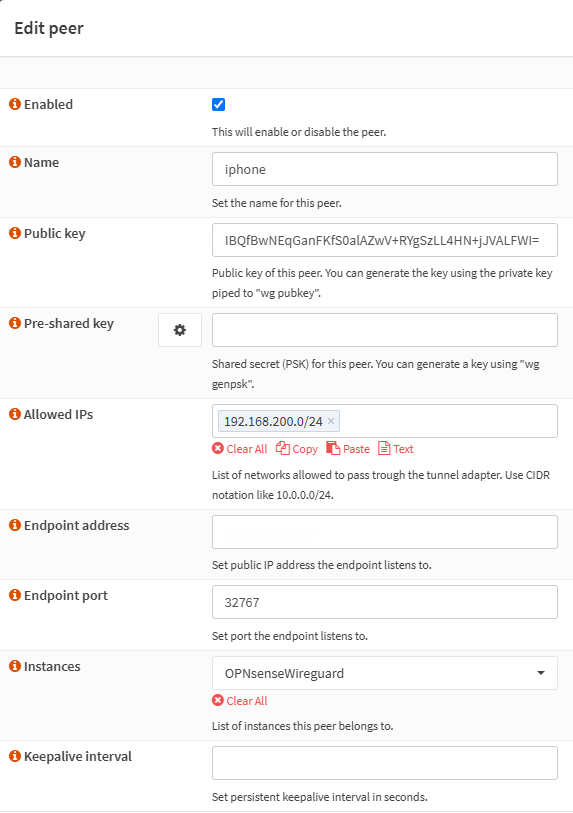
In OPNsense, go to VPN -> WireGuard -> Peers -> + Add
- Public key: iPhone WireGuard Public key
- Allowed IPs: WireGuard Tunnel IP address ranges coming from iphone
- 192.168.200.0/24 in this example.
- Endpoint port: Listen port number.
- 32767 in this example.
- Instances: WireGuard Instance name linked with this WireGuard peer.
OPNsense Firewall Rule
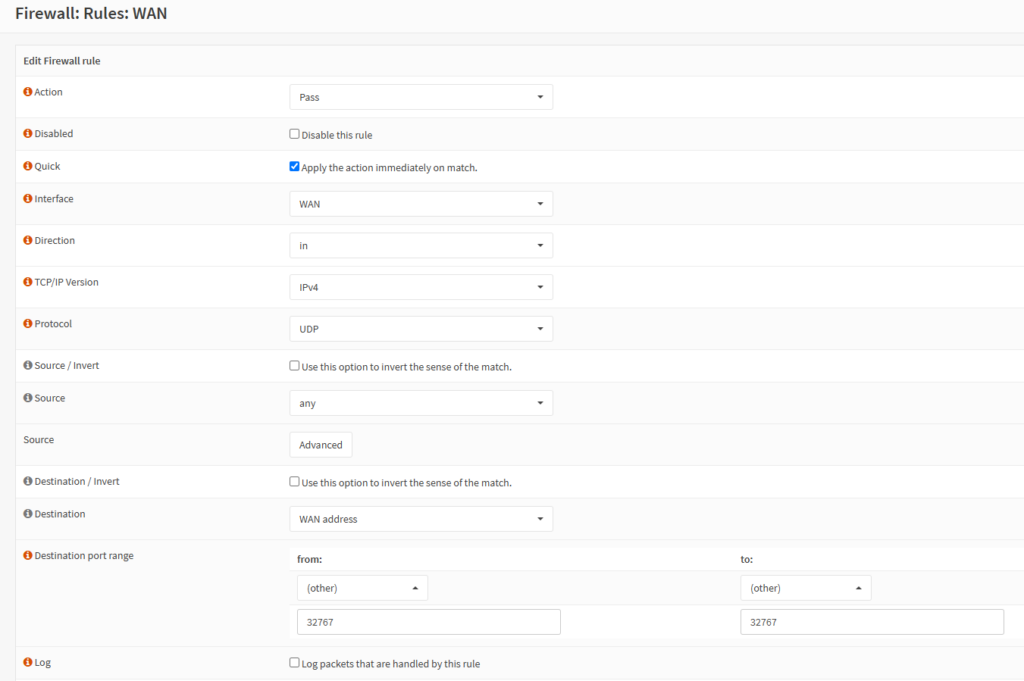
Without this rule, WireGuard traffic cannot pass through the WAN interface to establish a connection.
In OPNsense, go to Firewall -> Rules -> WAN -> + Add
- Action: Pass
- Interface: WAN
- WAN interface on OPNsense router
- Direction: in
- From Internet To WAN interface on OPNsense router
- TCP/IP version: IPv4
- Protocol: UDP
- WireGuard uses UDP
- Source: any
- any means anywhere from Internet
- Destination: WAN address
- WAN interface on OPNsense router
- Destination port range: from: to:
- Port number is the listen port of WAN interface on OPNsense router.
- 32767 in this example.
Remember to save and apply the rule after the change.
Troubleshoot
- Checking if WireGuard traffic is blocked by firewall.
- In OPNsense, go to Firewall -> Log Files -> Live View